Some time has gone by, and we’ve made a little progress on the DSi — at least, enough for some people to notice — so maybe I should write a little bit about it.
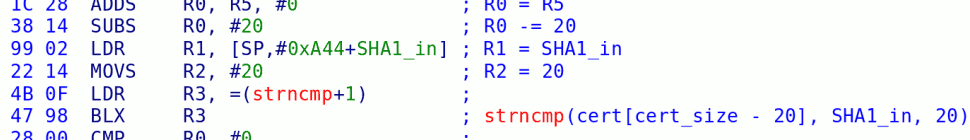
I personally haven’t had much luck with my DSi. I tried to dump the flash on it, and managed to blow a fuse in the process (it’s hard to keep that battery aligned with the case removed…). I can’t run any of the savegame hacks, because there are no DSi-mode cartridge-based games for the Japanese DSi yet. I decided to get a bit more aggressive and see if we could sniff the RAM:
This didn’t actually end up working out so well. The thing stopped powering on, and well, yeah.
I did have a little more luck dumping the SPI flash onboard the WiFi dongle:
I used Travis Goodspeed‘s awesome GoodFET device (thanks Travis!). Some of you may remember FlashMe on the older Nintendo DS — this was the program that let you reflash the “firmware” that was stored on the SPI flash on the WiFi daughtercard to e.g. bypass RSA verification of Wireless MultiBoot games. The DSi has the same chip in the same place, but it only holds a small amount of configuration data, with the “firmware” being stored elsewhere. Bummer.
Meanwhile, at least two people have successfully dumped the 256MB MMC NAND flash; in at least one case, an old SD card reader was just soldered to 4 vias on the PCB! We’ve learned that there is approximately 1MB of that flash chip dedicated to the “firmware” used to boot the DSi — more on that below — and that second-stage loader is encrypted with a key that is shared among all DSis and stored in ROM (much like boot1 on the Wii). Of that 1MB, about 300K is actually used. The remainder of the NAND flash is encrypted uniquely per console, so as with the Wii, you can’t take the contents of one flash chip and boot it on another console. (However, like with the Wii, it IS possible to back up your encrypted flash, upgrade or modify it, and then reflash back your old image to restore the old state. The nice part is that it only requires 4 wires to do so on the DSi, as compared to 16 on the Wii.)
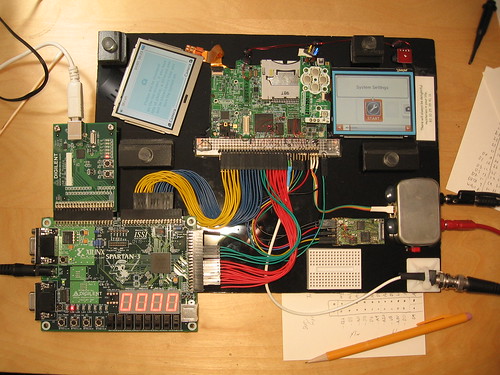
Once it became clear that something was seriously wrong with my DSi and it was never going to be useful in its current form, it gave its life to science. From that, we were able to find points to solder to all of the address, data and control lines on the DSi’s Pseudo-SRAM chip without removing any chips, and a promising new member of our close-knit community was able to successfully wire up a working DSi to an FPGA:
scanlime really does some excellent work; through a bit of EE cleverness, he was able to slow down the clock of the DSi enough such that he could sniff all of the RAM traffic and dump it over USB to his computer for analysis.
We have no grand master exploit, but have learned the following things:
- There is a considerable amount of ROM (128K+?) and RAM (1MB+?) inside the CPU
- The internal ROM is quite sophisticated, compared to that of the Starlet (boot0) — it is able to initialize both LCD panels, read from the SPI flash and the MMC NAND flash, and decrypt the contents of the 2nd-stage bootloader from NAND into internal RAM. If there is an error, it can display an error code on the top LCD.
- The second stage bootloader is analogous to boot2 on the Wii — it can read the TMD for the System Menu from the NAND filesystem and load the contents into memory. Like the Wii, the code seems to be stored in NAND unencrypted (inside an encrypted filesystem). Unlike the Wii, it seems to actually verify the contents and signature of the TMD before executing it.
- Most of the interesting keys seem to be stored inside internal RAM, safely out of reach from us. They are cleared when a cartridge is loaded, and probably even when a DSiWare app is loaded.
While this is a tremendous boon, there are still many challenges ahead. We have not yet found keys to decrypt most of the system software, and even finding those will not be enough to actually let us execute code; that will require a further exploit. Furthermore, we are currently drowning in data — a full RAM trace from scanlime’s setup from startup to installation of a channel is over 10 gigabytes. We have some software that can convert this into a RAM dump — please don’t even ask me for it — but most of the interesting bits are only stored in memory temporarily. Work is still ongoing to let us analyze the flow of memory accesses and pick out those interesting, ephemeral bits.
In some ways, this is similar to what happened with the Wii — fiddling with the RAM gave us much greater insight into how the system worked, but it still took several months of dedicated reverse-engineering before we had a usable exploit. Maybe this one will be faster, or maybe Nintendo will have learned a thing or two from their previous mistakes.


20 responses so far ↓
1 SquidMan // Sep 6, 2009 at 1:33 am
Nice post bushing. I’ve been hanging out in the dev channel, and you’ve actually told me things I never heard there? IS THERE A SEKRIT CHAN!? D:<
Back on track, yeah, it looks like Nintendo might've gotten a bit smarter this time around. But, like every software, it's gotta have a bug somewhere! :p
Best of luck, I'll keep hanging out, hopefully getting more fun info like this.
Also, keep writing these tech posts, I LOVE THEM :3
2 tim // Sep 6, 2009 at 5:43 am
its good to see you guys are still keeping this alive.
this is most interesting, and looks like you have a lot of things to do… cant wait!
keep up the awesome work guys!
3 DavidSmith417 // Sep 6, 2009 at 7:23 am
Thanks for the update, hopefully this will get our foot in the door to find a viable exploit for running homebrew.
4 tech3475 // Sep 6, 2009 at 9:24 am
Just to let you guys know, the first DSi only (possibly native) game has been announced:
http://www.teletext.co.uk/gamecentral/news/70868eea4c099e5ffaa5a3fd2f466005/Only+on+DSi.aspx
Hopefully there is a flaw in this which helps you guys.
5 Ibrahim Awwal // Sep 6, 2009 at 11:26 am
Cool, well, I guess we’ll have to wait for an exploit for some time yet. The current save game exploits probably require a homebrew cartridge anyway, right, to get the modified save on the system? I’m probably going to buy a DSi soonish before the free Nintendo points thing runs out, and I suppose I could help out with anything that doesn’t require me to take my DSi apart because I actually want to use it for games. I do have knowledge of assembly/computer organization and basic circuits stuff but no FPGAs yet.
6 someone // Sep 6, 2009 at 11:52 am
It looks like they’ve learnt a lot from the Wii, storing things like keys internally, wiping memory as soon as it’s not needed, and more consistency checks.
But nothing’s perfect, keep on at it and I’m sure you’ll crack it!
7 funkamatic // Sep 6, 2009 at 1:52 pm
whoa. I didn’t even know you guys were working on this. I feel for you and your DSi. May it rest in piece.
GOOD LUCK!!!
8 Mike // Sep 6, 2009 at 2:44 pm
wow, well close but far. you guys are awesome, i have been hoping for an update…. keep em coming.
9 PidGin128 // Sep 6, 2009 at 5:55 pm
I saw bits of this float by on hackaday, thanks for the details. your posts are really well executed.
Fortune: “There will always be delightful memories in your life. 83 10 25 39 41 11”. How appropriate, I laughed a bit when I got it. Too bad your unit had a shorter life.
10 WiiGamin // Sep 7, 2009 at 1:13 am
Very well done, guys! Finally getting some solid data! I love that RAM trace setup. It’s beautiful. It’s obvious that Nintendo has definitely made a much more sophisticated anti-hack setup for the DSi. Too bad about yours, though. RIP, little guy. I hope you find something soon! =)
11 tim // Sep 7, 2009 at 7:56 am
bushing, seems like you just took your DSi apart as it had no use, and now the first DSi game to be release will be for the JAP DSi… can you see the irony!?!
12 Wack0 // Sep 7, 2009 at 12:28 pm
nice, nice .. 🙂 so at least we know you are making progress on the DSi, if only a little .. oh and btw the DSi equivilant of boot2 checks the sig of whatever the titleID of the DSi-sysmenu is before running it ? obviously this is similar to boot1 on the Wii with it checking boot2’s sig before launching it 😛
13 Grayda // Sep 7, 2009 at 5:47 pm
nawww dude, if you could get the keys with a pair of tweezers, beef up the hack and do it with a set of kitchen knives. The bigger the equipment, the better the hax0rz, right?
Now, if only the students at my workplace could understand that you can’t “just do it” or “press more keys” to get it working.
I can’t wait to see some progress, even though I won’t be buying a DSi any time soon. Keep up the great work guys!
14 ifish // Sep 8, 2009 at 2:11 pm
nice post bushing
may you dsi rest in peices
15 radbme // Sep 8, 2009 at 6:46 pm
Seems to me Nintendo has learned from their previous mistakes with the Wii. However, where there is a will, there is a way.
16 Hells_Guardian // Sep 9, 2009 at 5:12 pm
Great info my good sir. By all means I’m definately looking forward to seeing what this team can come up with. You are some truely awsome hackers and your talents are quite great. I really do look forward to seeing something more from you gents.
BTW Great post. The wealth of information contained within looks quite promising. 🙂
17 HyperHacker // Sep 11, 2009 at 2:40 pm
That’s pretty awesome. If you can sniff RAM in real time though, why can you not modify it, injecting your own code?
18 Sotomura // Sep 15, 2009 at 4:30 pm
So the DSi does indeed have region locking? Does the DSi even attempt to boot the game? Does the DSi-compatible game just simply fail to load the DSi-specific features? What error pops up?
19 Temporal Hex Dump » Micah's Bloggy Widget // Jul 25, 2010 at 9:30 pm
[…] building some hardware to trace and inject data on the Nintendo DSi’s RAM bus, it became obvious pretty fast that there’s a lot of data there, and (as far as I know) no […]
20 DSi RAM tracing » Micah's Bloggy Widget // Jul 25, 2010 at 9:30 pm
[…] for The Homebrew Channel. Bushing has written a couple blog posts about our DSi efforts so far: one on the RAM tracing effort in general, and one with a sample […]
You must log in to post a comment.