You thought HBC was dead? Can’t say I blame you!
Our usualy update cycle tends to follow Nintendo’s updates: Nintendo plugs one of our exploits, and we release a new version with a new exploit. At the same time, you get all the new goodies and bugfixes that we may have accumulated since the previous version.
However, Nintendo’s care for the Wii lately has been rather sparse. We’ve been working on HBC every now and then behind the scenes: a bugfix here, a new feature there, and so on. Meanwhile, we waited and waited and waited for an update to break the current version. Alas, crickets.
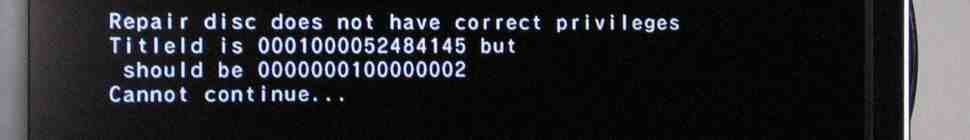
And yet! Recently, Nintendo did break The Homebrew Channel. No, it wasn’t a system update. It wasn’t a new Wii model (though they did release a new Wii, it turns out it works just fine). What they came up with was a new Wiimote, which, completely by accident, happens to be incompatible with the previous version of The Homebrew Channel.
You see, way way back in 2006 when the Wii came out, someone figured out that you could send commands to the Wiimote in a certain way. Libraries were developed, and eventually we had support on the Wii itself with the advent of Wii homebrew. And yet, nobody though to question the way we were sending the commands. Nobody bothered to check whether the Wii itself was doing the same thing.
As it turns out, it wasn’t. It was using a different method of sending data to the Wiimote. The Wiimote itself supported both – until the new RVL-CNT-01-TR model came out, that is. They probably had to trim the firmware to make space for the Motion Plus stuff.
HBC 1.0.8 was released 18 months ago, and we’re at over 3.1 million unique installs – that’s 3.4% of all Wiis sold to date, and this is only counting on-line HBC installs! Today, we bring you the HackMii Installer v1.0, featuring The Homebrew Channel v1.1.0 and BootMii 1.4. Here’s what you get:
- The new RVL-CNT-01-TR Wiimotes are now supported. Unfortunately, although HBC itself will work, there’s no way it can make existing homebrew work with it too – authors will have to recompile using the latest libogc SVN. C’est la vie!
- HBC now has a new font renderer with TTF support. The new renderer uses FreeType to render fonts with kerning and antialiasing, which looks much, much better than the old crummy bitmap font engine. You can use multiple fonts, sizes, and colors, under the control of a theme. The rendering is optimized for the screen resolution in use (4:3 or 16:9) for the best quality (note: this means the fonts will look a bit different between both modes, as they are hinted at different resolutions). The new default font is Droid Sans.
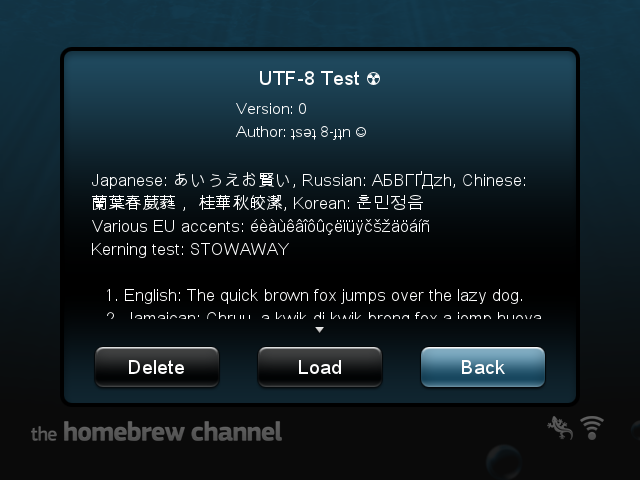
- Unicode (UTF-8) support. HBC has been using UTF-8 in meta files for a while, but only supported the latin-1 subset. Now you can display any character present in whatever font you’re using.
- HBCは日本語を話します! HBC wa Nihongo o hanashimasu! Yup, with Unicode support comes a Japanese translation, courtesy of JEEB. However, to enable it, you need to install a theme with a Japanese capable font. Check out the themes page to get it.
- While adding the new font engine we also fixed a bunch of underlying issues. The meta.xml system should now be quite a bit more tolerant and stable.
- We’ve added screenshot functionality for theme creators who want to show off their themes. Plug in your Nunchuk and press Z+C (in that order) to create a png screenshot on your SD card.
- The crashes when using no_ios_reload with a bad/disabled network config have been fixed – by removing
<no_ios_reload/>mode. Instead, we always reload IOS, but don’t fret – you can still use AHB access, thanks to a trick that we implemented. Use<ahb_access/>(<no_ios_reload/>is actually just an alias for that now). - “This update provides behind-the-scenes fixes that will improve the overall system performance”. And unlike Nintendo, we actually mean it; there’s an assortment of fixes for quite a few minor (and some not so minor) bugs and glitches, including those that come with the latest libogc and libfat (e.g. 4K sector support) and some issues when launching apps and hotplugging devices.
The full release notes with all the gory details are available on WiiBrew.
As usual, either grab the new installer here, or use The Homebrew Channel’s online update (a confirmation dialog should pop up when you start your current version, if you are connected to the Internet). Have fun!